¶ Welcome to the Snort Lab
¶ Overview
In this lab the soc will teach you how to install and setup snort on your device, how to foward those logs to your Splunk server, and the basic ruleset of snort
¶ Technologies that you will use
- Snort
- Splunk
- Splunk's Universal Forwarders
¶ Lab Structure
- We give you a task. We want you to figure out as much as you can by yourself so the instructions will be very minimal.
- If you're having trouble with a task, don't hesitate to check the hints section.
- Don't be discouraged as we also share the answers.
¶ Setup
You have 2 options for this lab. To follow along this lab you can either use the SDC cloud or use your local machine to build the lab. I recommend the SDC cloud as it is simpler than trying to install your own virtual machine on your own computer.
¶ Warning!!!!
-
This lab assumes that you completed the Splunk lab and have atleast the basic understanding of how to set up the forwarders.
-
This lab takes place in Ubuntu if you use another Linux distro, it might be different
¶ 1. Installing Snort
Snort works best on Ubuntu.
Let's start by installing it on bash.
Hint: Need help installing Snort?
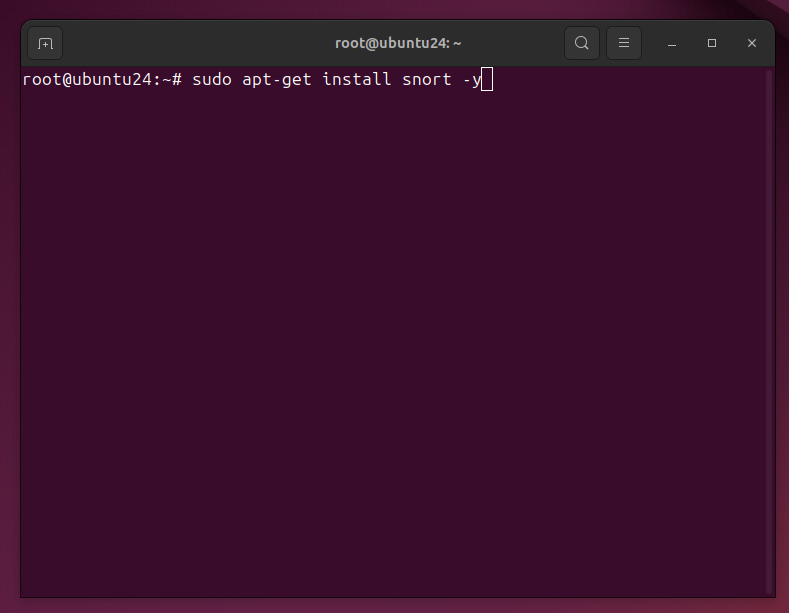
sudo apt-get install snort -y
Run the command above to install Snort. This uses apt-get, the Ubuntu package manager, to automatically download and install Snort with a yes flag (-y).
¶ 2. Setting the Network Interface
Once Snort is installed, you'll need to configure the network interface.
In this example, we'll use the IP address 10.128.69.150 for the lab.
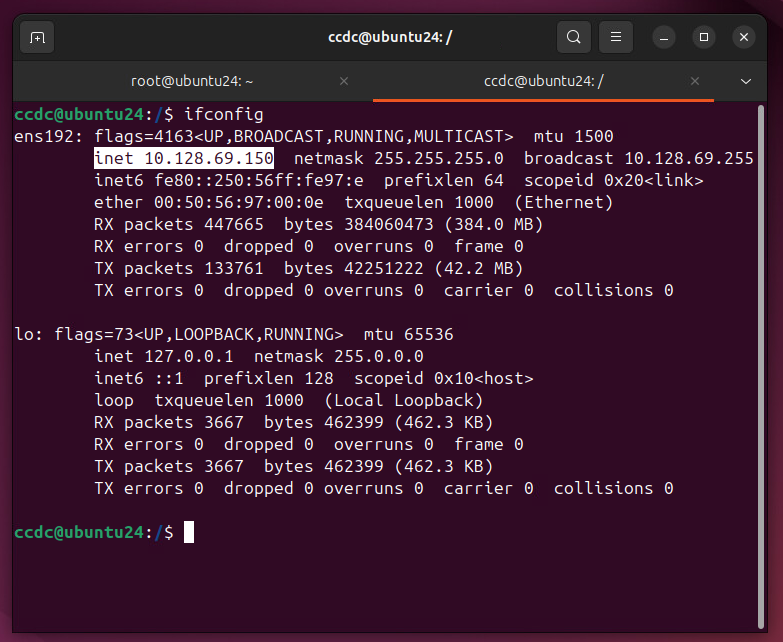
¶ Step:
Set your network interface IP to {YOUR IP ADDRESS}.
Hint: Need help with setting up/finding the IP?
- Find the IP address of your network interface with the bash commandifconfig
or
ip addr
- Modify the configuration to use
{YOUR ADDRESS}/24which encompasses the subnet.
¶ 3. Enable Promiscuous Mode
Turn on promiscuous mode for Snort to detect traffic.
Hint: How to set it up
sudo ip link set {YOUR INTERFACE} promisc on
Hint: What does promiscuous mode do?
Promiscuous mode allows Snort to monitor all traffic on the network, not just traffic directed to the specific machine.¶ 4. Editing the Snort Configuration File
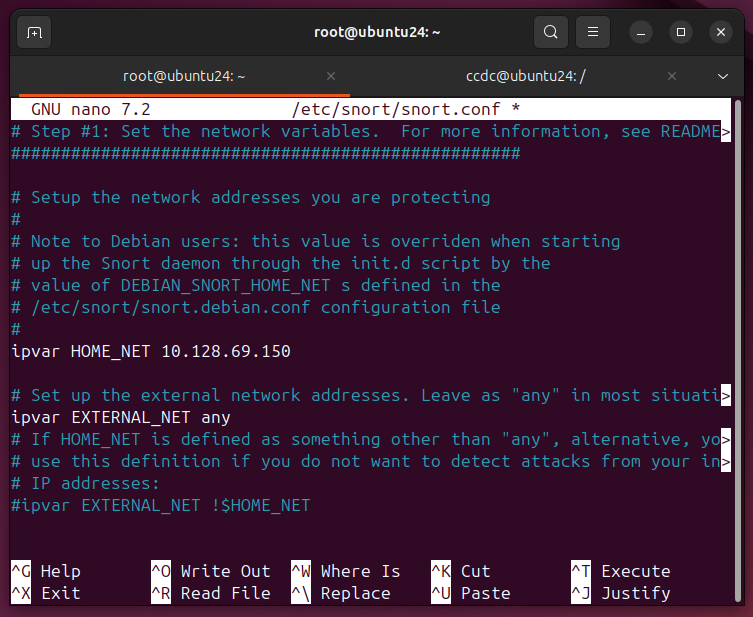
You will now need to edit Snort's configuration file and insert the ip address of your snort server
Hint: Don't have a text editor for some reason?
```bash sudo nano /etc/snort/snort.conf ```ipvar HOME_NET any
ipvar HOME_NET {THE SERVERS IP ADDRESS}
Hint: Don't have a text editor for some reason?
If `vim` or `gedit` are not installed, run: ```bash sudo apt-get install vim -y sudo apt-get install gedit -y ``` Then you can open the Snort configuration file.¶ 5. Test the Configuration
After editing, let's test the configuration.
sudo snort -T -i ens33 -c /etc/snort/snort.conf
Hint: What does the command do?
This command tests the Snort configuration using the interface `ens33` and the configuration file located at `/etc/snort/snort.conf`.¶ 6. Creating Local Rules
Now, let’s create a local rule for Snort to trigger an alert.
sudo nano /etc/snort/rules/local.rules
¶ Example Rule:
Create a rule to detect an ICMP ping:
alert icmp any any -> $HOME_NET any (msg: "ICMP Ping Detected"; sid: 100001; rev:1;)
Hint: What does this rule do?
This rule will alert if an ICMP ping (commonly used in `ping` requests) is detected. It logs with a message "ICMP Ping Detected" and assigns it a `sid` (Snort ID) of `100001`.¶ 7. Running Snort with the Rule
Now let’s run Snort with the rule you just created.
sudo snort -q -l /var/log/snort -i ens33 -A console -c /etc/snort/snort.conf
Hint: What do these options mean?
- `-q`: Quiet mode (suppresses unnecessary output). - `-l /var/log/snort`: Logs will be stored in `/var/log/snort`. - `-i ens33`: Specifies the network interface to listen on. - `-A console`: Outputs alerts to the console. - `-c /etc/snort/snort.conf`: Uses the configuration file from the given path.¶ 8. Testing the Rule
To test the rule, you can try pinging the configured IP from another machine:
ping 10.128.69.150
Hint: How to check if it worked?
If the ping is detected, you should see an alert message like: `"ICMP Ping Detected"` in the Snort logs and on the console.¶ 9. Forwarding Logs to Splunk
Now, we will forward Snort logs to Splunk using a Splunk universal forwarder.
¶ Step 1: Add the Snort log directory to Splunk.
cd /opt/splunkforwarder/bin
sudo ./splunk add monitor /var/log/snort/alert
Hint: What's happening here?
This adds `/var/log/snort/alert` as a monitored file for Splunk, so it will forward log data to your Splunk instance.¶ 10. Configure the Splunk Forwarder
Edit the Splunk configuration file to include the proper inputs.
sudo -i
cd /opt/splunkforwarder/etc/apps/search/local
nano inputs.conf
¶ Add the following input configuration:
[splunktcp://9997]
connection_host = <Splunk_IP_Address>
[monitor:///var/log/snort/alert]
disabled = false
index = snort
sourcetype = snort_alert_full
source = snort
Hint: What do these configuration lines mean?
- `splunktcp://9997`: Specifies the Splunk port used for receiving data. - `connection_host`: This is the IP address of your Splunk server. - `monitor`: This line monitors the Snort alert file and forwards it to Splunk. - `index`: Indicates where the data will be indexed (e.g., `snort` index). - `sourcetype`: Defines how the data will be classified in Splunk (e.g., `snort_alert_full`).Now you’ve successfully set up Snort, created a local rule, and forwarded logs to Splunk! Create your own rulesets and learn how to get more out of it!
wrote by
bruhberto ^-^